How To Ensure Cybersecurity in Industrial Machine Connectivity
Key considerations and best practices for protecting machine data and ensuring secure operations.

Table of Contents:
- Introduction
- Understanding cybersecurity threats in industrial machine connectivity
- Key cybersecurity principles for industrial machine connectivity
- Best practices for securing industrial machine connectivity
- Incident response and threat mitigation in OT security
- How Reniver helps secure industrial machine connectivity
- Conclusion and next steps
1. Introduction
As industrial systems become more connected, the risk of cyberattacks on manufacturing and production facilities has significantly increased. Traditionally, Operational Technology (OT) networks operated in isolation, but modern industrial automation now requires machine-to-machine communication, remote access, and cloud integration. While this improves efficiency, it also exposes industrial systems to cyber threats that were once limited to IT environments.
Recent high-profile cyberattacks have demonstrated just how vulnerable industrial companies are:
-
Duvel Moortgat (2024) - The brewery was forced to halt production and shut down operations due to a cyberattack targeting its IT and OT systems.
-
Schneider Electric (2024) - A hacker claimed to have stolen 40GB of critical company data, exposing potential security risks in industrial automation.
-
JBS Foods (2021) - A ransomware attack disrupted global meat production, forcing the company to pay a $11 million ransom to regain access to its systems.
-
Colonial Pipeline (2021) - A cyberattack on the fuel supplier's industrial control network led to fuel shortages across the U.S.
-
Picanol (2020) - A ransomware attack halted production across multiple sites in Belgium, China and Romania. The attackers demanded a ransom in exchange for restoring access to critical systems and restarting machine operations.
These incidents show that cyberattacks on industrial environments are not rare exceptions, they are becoming common occurrences. Attackers target manufacturing plants, production facilities, and industrial supply chains, often leading to complete operational shutdowns, financial losses, and reputational damage.
This article explores the key cybersecurity threats in industrial machine connectivity, the best practices for securing industrial networks, and the technical solutions to mitigate cyber risks in manufacturing environments.
2. Understanding Cybersecurity Threats in Industrial Machine Connectivity
Industrial environments face unique cybersecurity threats due to the increased connectivity between OT (Operational Technology) and IT networks. Many industrial control systems (ICS) were never designed with security in mind, making them vulnerable to unauthorized access, malware, and data breaches. Below are the most common attack vectors that threaten industrial machine connectivity.
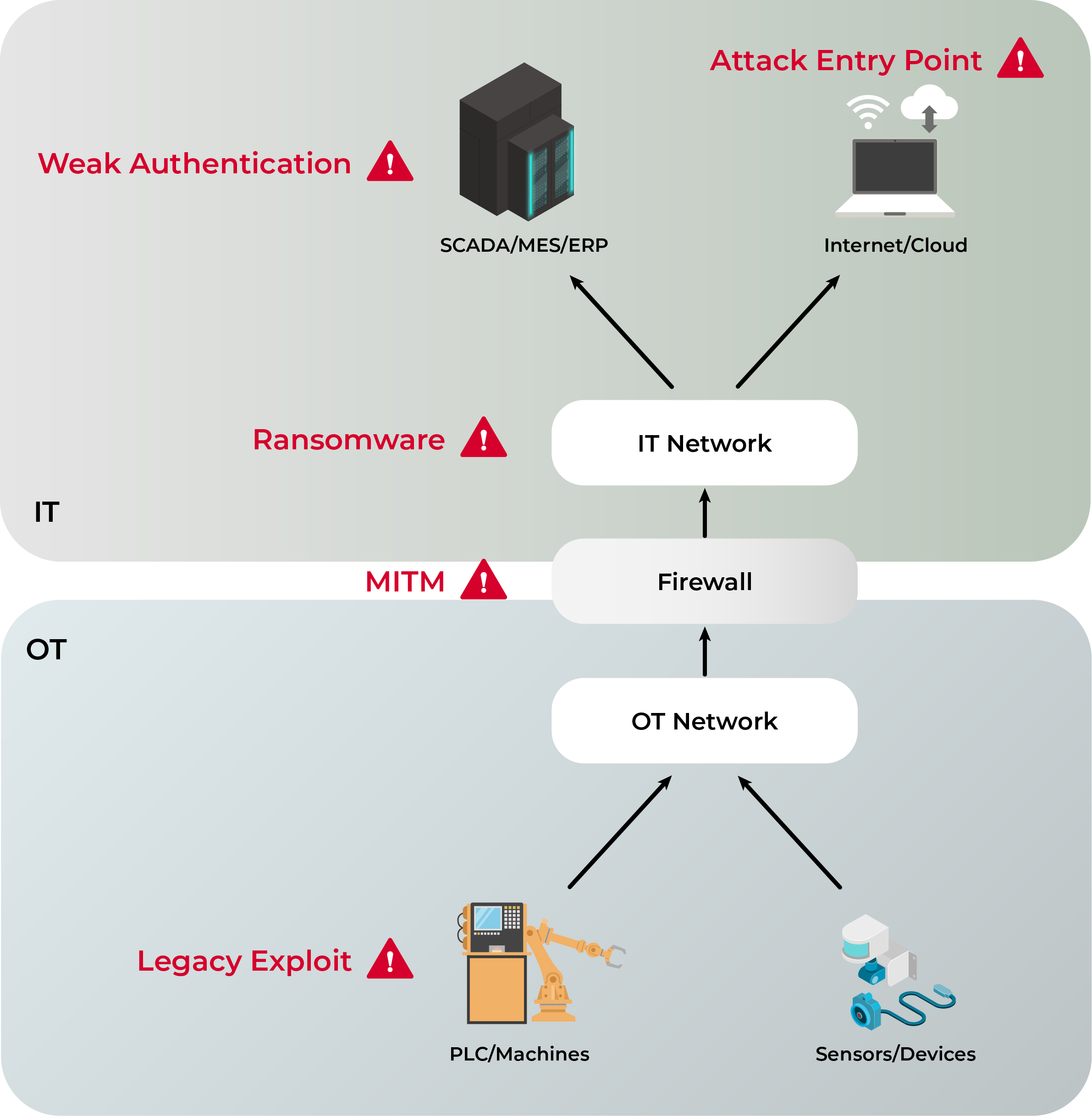
Unauthorized access and weak authentication
Many industrial systems still rely on default passwords, outdated authentication methods, or unsecured remote access. Attackers exploit these weaknesses to gain control over machines, alter production parameters, or shut down operations.
- Example: In 2021, a hacker attempted to increase the sodium hydroxide levels in a Florida water treatment facility by exploiting weak authentication controls.
Man-in-the-Middle (MITM) attacks
Without encryption, machine-to-machine (M2M) communication can be intercepted and altered by attackers. This allows hackers to manipulate sensor data, send false commands to machines, or disrupt production processes.
- Example: MITM attacks on unsecured MQTT or OPC UA traffic can inject false data into SCADA systems, causing operational failures.
Malware, ransomware, and industrial espionage
Ransomware attacks encrypt industrial systems, forcing companies to pay large sums to restore operations. Malware infections can also be used for data theft, sabotage, or long-term espionage.
- Example: The Norsk Hydro ransomware attack (2019) crippled global aluminum production, forcing manual operations for weeks.
Legacy system vulnerabilities
Older machines often run outdated, unpatched firmware with known vulnerabilities. Since some legacy systems cannot be updated without disrupting production, they become easy entry points for attackers.
- Example: The Stuxnet attack (2010) targeted Siemens PLCs running outdated software, proving how vulnerable legacy machines can be.
Working with legacy machines that weren't built for connectivity? Learn how to integrate them securely and efficiently in our article on legacy machine integration.
Supply chain attacks
Hackers exploit third-party software, hardware, or remote maintenance connections to infiltrate industrial networks. Attackers may inject malicious code into software updates or compromise suppliers with lower security standards.
- Example: The SolarWinds attack (2020) allowed attackers to access thousands of enterprises and industrial systems worldwide by exploiting a compromised software update.
Next: Key cybersecurity principles for industrial machine connectivity
Cyber threats in industrial environments cannot be eliminated, but they can be mitigated with strong cybersecurity practices. The next section outlines foundational security principles that help protect machine networks from these risks.
3. Key Cybersecurity Principles for Industrial Machine Connectivity
Industrial cybersecurity requires a structured, proactive approach to mitigate risks while ensuring seamless machine operations. Implementing core security principles helps prevent unauthorized access, data manipulation, and operational disruptions without affecting system performance.
Zero Trust Architecture (ZTA): Never trust, always verify
Traditional OT networks relied on implicit trust, assuming that devices inside the network were secure. Zero Trust eliminates this assumption by requiring continuous verification of users, devices, and system interactions.
-
Enforce strict authentication before granting access to any industrial system.
-
Require multi-factor authentication (MFA) for remote and privileged users.
-
Apply device identity verification to prevent unauthorized machines from joining the network.
Defense in depth: Layered security for industrial systems
A single security measure is never enough. Defense in Depth applies multiple overlapping security layers, ensuring that even if one layer is breached, attackers cannot move freely.
-
Network Layer: Use firewalls, VLAN segmentation, and intrusion detection systems (IDS/IPS).
-
Device Layer: Keep firmware updated and apply secure boot mechanisms to prevent unauthorized code execution.
-
Application Layer: Encrypt industrial protocols like OPC UA and MQTT to prevent data interception.
Least Privilege Access (LPA): Restrict system permissions
Many cyberattacks exploit overly permissive access controls in OT environments. Implementing Least Privilege Access (LPA) ensures that users and devices only have access to what is necessary for their role.
-
Use Role-Based Access Control (RBAC) to assign permissions based on job function.
-
Restrict remote access to authorized users only, using secure VPNs and dedicated jump servers.
-
Implement read-only access for systems that do not require active modifications.
Real-time monitoring & anomaly detection
Even with strong preventive measures, cyber threats can evolve. Continuous network monitoring helps detect suspicious activity, unauthorized access attempts, and malware infections before they cause damage.
-
Deploy Security Information and Event Management (SIEM) tools to collect and analyze security logs.
-
Use behavioral anomaly detection to identify unusual machine activity or data traffic.
-
Implement automated alerting systems to notify security teams of potential breaches.
Next: Best practices for securing industrial machine connectivity
With these foundational security principles in place, the next step is to implement specific best practices for network segmentation, secure authentication, data encryption, and legacy system protection which are all covered in the following section.
4. Best Practices for Securing Industrial Machine Connectivity
In connected industrial environments, applying cybersecurity principles requires concrete technical measures. These best practices address core areas of vulnerability in machine communication, access control, and system architecture, ensuring security measures are both practical and compatible with operational requirements.
Network segmentation and secure architecture
Keeping IT and OT systems isolated helps contain security incidents and limits exposure.
-
Segment OT networks from corporate IT using firewalls and DMZs (demilitarized zones).
-
Use VLANs to isolate production lines, devices, or departments.
-
Place high-risk devices (e.g. legacy machines) in restricted zones with limited communication paths.
This structure minimizes lateral movement in case of an intrusion.
Strong authentication and access control
Preventing unauthorized access is essential for maintaining control over machine systems.
-
Enforce Multi-Factor Authentication (MFA) for remote access and administrative roles.
-
Implement Role-Based Access Control (RBAC) to assign only the necessary permissions.
-
Avoid shared credentials, and log all access events for audit purposes.
These measures reduce the likelihood of privilege misuse or unauthorized system changes.
Secure data transmission and encryption
Unencrypted machine communication is vulnerable to interception and manipulation.
-
Use TLS/SSL encryption for protocols like OPC UA, MQTT, and HTTPS.
-
Implement certificate-based authentication between clients and servers.
-
Encrypt both data in transit and at rest, especially when storing sensitive operational data locally or in the cloud.
This protects data integrity and confidentiality across the entire communication chain.
Patching and isolating legacy systems
Legacy machines often can't be updated but still need to be secured.
-
Where patching is possible, maintain a controlled update schedule during maintenance windows.
-
For unpatchable systems, isolate them using network segmentation and firewall rules to restrict communication.
-
Monitor legacy devices for anomalous behavior using intrusion detection systems.
Virtual patching such as enforcing security controls at the network level can help protect legacy systems without disrupting production.
Protecting against supply chain attacks
Third-party components are a growing source of risk in industrial environments.
-
Work only with verified hardware and software vendors that provide regular security updates.
-
Conduct security assessments of suppliers, especially those with remote access or integration into your OT network.
-
Implement code signing and integrity checks to verify software updates.
Managing the supply chain reduces the risk of introducing vulnerabilities from external sources.
Next: Incident response and threat mitigation in OT security
Even with strong protections in place, incidents can still occur. The next section focuses on incident response planning, monitoring, and recovery strategies to contain and mitigate the impact of cyber threats.
5. Incident Response and Threat Mitigation in OT Security
Despite careful planning and strong preventive controls, industrial networks remain exposed to risks. When a security event does occur, the speed and structure of your response will determine how well damage is contained and operations are restored. For OT environments, this means having specialized tools, processes, and procedures ready to handle threats without compromising uptime or safety.
Establish a cyber incident response plan
An OT-specific incident response plan ensures that teams know how to act when a breach occurs.
-
Define clear roles and responsibilities for operations, IT, and cybersecurity personnel.
-
Include procedures for containment, eradication, and recovery.
-
Test the plan regularly with simulated incidents or tabletop exercises.
This ensures that your team can respond quickly and effectively under pressure.
Deploy real-time monitoring and alerting tools
Detecting a threat early is critical for reducing its impact.
-
Use Security Information and Event Management (SIEM) systems to aggregate and analyze log data.
-
Deploy Intrusion Detection Systems (IDS) on OT networks to monitor unusual traffic patterns.
-
Establish threshold-based alerts for unauthorized access attempts, unexpected network behavior, or device anomalies.
These tools help detect threats before they escalate into full-blown incidents.
Conduct vulnerability assessments and penetration testing
Identifying weaknesses before attackers do is a key part of any defensive strategy.
-
Perform regular vulnerability scans on industrial devices and network infrastructure.
-
Work with security specialists to conduct penetration tests on isolated OT environments.
-
Prioritize remediation based on risk and operational impact, especially for critical assets.
This proactive approach helps close security gaps before they can be exploited.
Maintain secure backups and recovery procedures
If a system is compromised, having secure, recent backups is essential for restoring operations.
-
Store backups offline or in segmented environments to protect them from ransomware.
-
Test recovery processes regularly to ensure backups are usable and complete.
-
Document failover procedures for critical systems to minimize downtime during recovery.
A tested recovery plan ensures business continuity even in worst-case scenarios.
Next: How Reniver helps secure industrial machine connectivity
With monitoring, response, and recovery capabilities in place, the next step is identifying trusted partners and solutions that can help implement and maintain strong cybersecurity in industrial environments. The following section introduces how Reniver supports organizations in securing machine connectivity.
6. How Reniver Helps Secure Industrial Machine Connectivity
At Reniver, cybersecurity isn't an afterthought, it's built into the core of our connectivity solutions. We help industrial companies integrate machines securely and reliably through a combination of trusted technologies, standardized protocols, and secure deployment practices.

Secure by design: Edge gateway and Reniway platform
Reniver's Edge Gateway and Reniway platform are designed to run fully local, allowing you to process and manage machine data without relying on constant cloud access. This local-first approach minimizes exposure to external networks, reducing the attack surface while preserving full operational control.
Standardized, secure protocols
We use OPC UA, a widely adopted industrial standard that includes built-in encryption, authentication, and role-based access control. By relying on vendor-neutral, well-supported protocols, Reniver ensures that machine data is exchanged securely and consistently across all connected systems, whether it's IIoT software, MES, or cloud analytics.
Isolation, control, and transparency
With Reniver's architecture:
-
Data stays within your environment unless you choose to send it out.
-
Access is strictly managed through configurable roles and permissions.
-
Communication between machines and systems follows encrypted, structured protocols, with no custom, untraceable data flows.
Whether you're connecting a new system or retrofitting legacy machines, Reniver gives you full control over your machine data, ensuring it's collected, standardized, and transferred securely without compromising uptime or flexibility.
Next: Conclusion and next steps
Cybersecurity in industrial machine connectivity is complex but it's manageable with the right tools and practices. In the final section, we'll recap key takeaways and explain how to take the first step toward securing your machine network.
7. Conclusion and Next Steps
Securing industrial machine connectivity is no longer optional,it's a critical part of maintaining safe, reliable, and future-ready operations. As connectivity expands between machines, systems, and cloud platforms, so do the risks. Addressing these challenges requires a combination of technical controls, best practices, and secure architectures.
Key Takeaways:
-
Industrial environments face specific threats such as unauthorized access, protocol vulnerabilities, and ransomware.
-
Core principles like Zero Trust, Defense in Depth, and Least Privilege Access should guide all security decisions.
-
Best practices, network segmentation, strong authentication, data encryption, and legacy system protection are essential for reducing attack surfaces.
-
Effective incident response requires real-time monitoring, tested recovery plans, and proactive vulnerability assessments.
How to move forward
Start by assessing your current OT security posture and identifying where vulnerabilities may exist, from legacy machines to network boundaries. Implement incremental improvements that align with both operational goals and cybersecurity standards.
Need help putting it into practice?
Reniver can support you with:
-
Secure edge connectivity via Reniway and our Edge Gateway
-
Local-first architecture with encrypted, standards-based communication
-
Expert guidance on implementing security in complex industrial environments
Contact us to discuss your industrial cybersecurity needs, or explore how Reniway Edge can help you build secure, scalable machine connectivity from the ground up.